Cybersecurity Services
Is the timing right to outsource your cybersecurity?
What business outcomes are you looking to achieve?
Thrive can help.
Complex cyber risk mitigation, simplified. Today’s complex cyber threats require a multi-solution approach combined with advanced skill sets and real-time, 24/7 monitoring. Thrive’s leading security platform integrates best in breed technologies, analyzing attack data with AI and certified security analysts to prevent the impacts from threats allowing you to focus on critical business outcomes.
Our security team combines the power of automation for rapid response and remediation with the expertise of our staff to address complex issues intelligently.
Trusted Cybersecurity Partners
Thrive offers NextGen cybersecurity solutions and services designed to meet the needs of your business.
Managed Detection and Response Service (MDR)
As critical security issues continue to pose a 24×7 risk to enterprise technology systems, you need a comprehensive Managed Detection and Response solution that scales, can flexibly meet changing needs and demands, and provides clear, actionable information.
Thrive’s MDR platform collects telemetry and data from servers, firewalls, network devices, applications, SaaS, Cloud, and security platforms, and adds real-time context, analytics, and alerts for a more complete understanding of the environment. When a suspicious incident is detected, pre-planned, automated responses are initiated to drastically reduce the time to respond to critical incidents. Analysis and triage are then performed by the 24x7x365 Thrive Security Operations Center (SOC) team of certified security experts to determine the threat risk and the appropriate actions to remediate or mitigate the threat.
Key Benefits:
- Improved Threat Detection and Response Capabilities.
- By detecting and responding to threats in real-time, Thrive MDR can help prevent data breaches and other cyber-attacks.
- Thrive MDR can help organizations comply with industry regulations and standards, such as GDPR, HIPAA, and PCI-DSS.
- Thrive MDR can help organizations save costs by reducing the need for multiple layers of cybersecurity resources and preventing major business-impacting data breaches.
Autonomous Penetration Testing
Autonomous penetration testing tools work by scanning the target system for weaknesses, analyzing the results of the scan, and then attempting to exploit any vulnerabilities found.
Thrive provides either a one-time autonomous penetration test or a recurring quarterly or monthly assessment to identify areas of risk, and provides both a Penetration Test Results report and Fix Actions report that outlines the steps required to eliminate the risk. A Thrive Consultant will review the test outputs with you to provide feedback and strategic recommendations.
Benefits:
- Find weaknesses in systems before attackers do
- Determine the robustness of controls
- Support compliance with data privacy and security regulations (e.g., PCI DSS, HIPAA, GDPR)
- Provide qualitative and quantitative examples of current security posture and budget priorities for management
Managed NextGen Firewall & Unified Threat Management
Thrive’s Managed NextGen Firewall service provides perimeter security and network performance that meets the requirements of any size SMB or Enterprise client. The service is delivered on the Fortinet Fortigate™ Next Generation Firewall platform which offers a robust set of security features with unmatched Unified Threat Management capabilities — all monitored and managed 24x7x365 by Thrive’s Network and Security Operations teams.
Optional Managed NextGen Firewall Services include:
- Intrusion Prevention Service
- Application Control and Web Filtering
- Gateway Antivirus and Antispam Email Security
- Site to Site and Remote Access Virtual Private Networking
- High Availability
- Software-Defined Wide-Area Networking (SD-WAN)
Vulnerability Management and Advanced Patching Service
Vulnerability Management is a key security control and formidable mitigation against security threats. Thrive’s Vulnerability Management service identifies software vulnerabilities through recurring scanning and analysis. Thrive’s Security Analysts consult with you to prioritize and address existing vulnerabilities before they can be exploited.
Thrive’s Advanced Software Patching service provides proactive remediation of security vulnerabilities through scheduled vendor updates to operating systems and other software applications. Thrive’s engineers test and validate patches before they are applied to your servers and end-user workstations and apply the updates during scheduled patching windows.
Endpoint Detection and Response
With the proliferation of sophisticated malware such as fileless attacks and zero-day executables, traditional signature based anti-virus and anti-malware technologies are unable to provide protection against these advanced threats and are reliant on updated signature databases of known threats.
Thrive’s Managed Endpoint Detection and Response service provides proactive, real-time, fully automated security with orchestrated incident response across all devices covering current and legacy operating systems.
It is the ONLY endpoint protection platform that delivers threat protection both pre- and post-infection in real time.
Here’s How Thrive’s Endpoint Detection and Response Protects Your Business:
- Protection, detection and remediation of file-based and fileless malware
- Real-time automated prevention of ransomware encryption
- Data exfiltration detection and protection
- Attacks surface reduction
- Automated remediation
- Off-line protection
- Network traffic analysis
- Direct link to alert Thrive’s 24x7x365 Security Operations Center on malicious or suspicious events
- USB blocking functionality
End User and Workstation Security
Advanced Email Security
Thrive’s Advanced Email Security provides protection against email-borne threats such as viruses, malware, trojans, malicious URLs, and weaponized attachments. Inbound, outbound, and internal email messages are inspected, while unsafe or malicious content is automatically removed before it reaches your network. Sensitive and confidential information can be protected from accidental or intentional exposure through encrypted email and Data Loss Prevention technologies.
Thrive Anti-Phishing and Security Awareness Training
People are the weakest link in the security chain. Technology and policy can be overcome by mistakes and lack of situational awareness. Cybersecurity attacks including Phishing and Spear Phishing are common methods of social engineering that cybercriminals use to gain access to critical systems and data, easily bypassing security controls by obtaining access and credentials of legitimate users.
Thrive Anti-Phishing and Security Awareness Training ensures your employees understand the mechanisms of spam, phishing, spear phishing, malware, ransomware and social engineering using training materials and targeted user campaigns aimed at improving awareness of and response to security threats.
Incident Response & Remediation
Thrive Incident Response & Remediation provides on-demand security response services to contain and remove threats, along with engineering assistance to rebuild and restore critical systems. The service provides faster recovery time from a cybersecurity incident so that the costs associated with business disruption are minimized.
With a Thrive Incident Response Retainer in place, companies can benefit from the Thrive team’s preparation, expertise, and responsiveness through:
- Pre-Incident Planning
- Incident Response Tools
- Compromise Assessment
- Prioritized Incident Management
Cybersecurity Bundle
Thrive’s End User Cybersecurity Bundle leverages best-in-class security products from multiple security platforms to deliver a holistic end-user security solution that provides a multi-layer defense to protect your users from advanced threats.
- Thrive Endpoint Security and Response
- Email Security, Remediation & Continuity
- Security & Phishing Awareness Training
- Secure Web Gateway

Driving Better Business Outcomes
“I can’t overstate how impressed we were with Thrive’s approach. The efficiency and expertise they brought to the table was remarkable.”
– John Ross, CIO, EXO Inc.
Hear from Our Customers
Managed Cybersecurity Services and Solutions for Your Business
Thrive, a leading managed cybersecurity service provider offers a range of comprehensive solutions aimed at safeguarding your entire IT environment. From endpoints to the Cloud and everything in between, Thrive’s dedicated security team designs and deploys effective security measures. Our tailored cybersecurity solutions ensure end-to-end protection for your systems and data, relieving the burden on your internal IT teams. As a managed Cybersecurity service provider, we help protect enterprises across various industries, including financial, healthcare, legal, insurance, life sciences/biotech, hospitality, manufacturing, government, and construction.
With Thrive as your managed security services provider, you can stay one step ahead of potential threats. Our expert team combines the power of automation for rapid response with the expertise of our staff to address complex issues intelligently. Operating round the clock, 24x7x365, our Security Operations Centers (SOC) deliver lasting solutions that proactively safeguard your business.
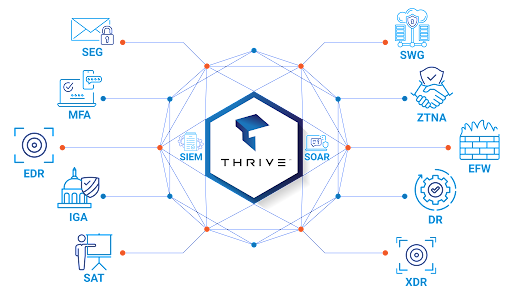
Thrive's Cybersecurity Mesh Architecture (CSMA)
Thrive supports clients and their ever-changing threat surface by constantly evaluating and improving our people, processes, and the technologies that are connected through our cybersecurity mesh.
Thrive’s Cybersecurity Mesh Architecture reduces gaps by connecting siloed solutions with two-way integrations that pull data into the mesh and push actions out to a wide range of tools. Thrive’s cybersecurity mesh includes threat intelligence and integrated defense tools to anticipate and prevent attacks. Using automation and orchestration, Thrive adds more context and faster connections between tools so that enforcement decisions align with the speed of business.
What Is Your Security Risk Exposure?
Did you know it takes organizations around 6 months to identify breaches? That amount of time with unprotected data can be detrimental to businesses in financial, healthcare, legal, education, government sectors, and more. We understand the stakes are high with these highly regulated industries. Failure to meet HIPAA and financial regulations can result in serious penalties such as fines, contract loss, or even a license withdrawal. In addition, it’s a big undertaking to meet all the legal and operational obligations, including compliance audits, access management, data encryption, network and computer security training, implementing new technology and more while protecting data.

Be Prepared with Incident Response and Remediation
Phishing, ransomware, and other cyberattacks put businesses of every size at huge risk of losing millions of dollars trying to remedy the situation. This kind of cost is unfathomable for many businesses – especially small to mid-sized enterprises, who simply cannot afford to pay out such a vast sum.
To help customers mitigate risk and avoid the rising costs of security threats, Thrive Incident Response & Remediation provides on-demand security response services to contain and remove threats, along with engineering assistance to rebuild and restore critical systems. The service provides faster recovery time from a cybersecurity incident so that the costs associated with business disruption are minimized.
With a Thrive Incident Response Retainer in place, companies can benefit from the Thrive team’s preparation, expertise, and responsiveness through:
- Pre-Incident Planning
- Incident Response Tools
- Compromise Assessment
- Prioritized Incident Management


Stay Ahead of Threats with Thrive
Thrive’s managed cybersecurity solutions leverage the deep expertise of the Thrive team to deliver proactive security that keeps customers ahead of threats. Thrive takes a hybrid approach using automation for speed and responsiveness combined with our expert staff for intelligent problem-solving and lasting solutions that are delivered 24x7x365 from Thrive’s Security Operations Centers (SOC).
Prevent data theft and ransomware damage in real-time, automatically. Take the next step to learn more about how Thrive can protect your business so you can focus on your customers.
The Thrive Cybersecurity Advantage
Thrive takes a customer-first cybersecurity approach based on the quality of its people and its architecture. When entrusted to fully manage a customer’s IT environment, from security, to collaboration, to the Cloud, Thrive enables often short-handed IT teams to focus on delivering results to core business operations. As a single point of control and communications across the IT landscape, Thrive can address issues without the coordination of multiple vendors as Thrive brings all of the pieces to the puzzle together.
Advantages include:
- Security Experts: Thrive’s Security Operations Centers (SOCs) are staffed by expert Certified Information Systems Security Professionals (CISSPs) and security professionals with decades of experience protecting mission-critical infrastructure
- Flexible Solutions: Unbundled managed services enable you to create a solution tailored to your exact needs, utilizing leading technology from Fortinet, Microsoft, Cisco, Mimecast, and more
- SOC Monitoring: Threats never rest, and neither do we. Thrive’s 24×7 SOCs monitor core critical infrastructure and security threats for businesses across the globe
Ready to Speak with Our Cybersecurity Experts?
Contact Thrive today and learn how we can deliver continuous, round-the-clock protection against both everyday and emerging threats, safeguarding your business’s productivity.









